What exactly is IAM?
IAM is a permission system that controls access to AWS resources, as the name indicates. So, as an administrator, it aids you in defining who has access to what on an AWS account.
Second, IAM users enable you to provide wide or particular rights to groups or even individual individuals. Broad permissions may include things like granting access to a complete AWS service, such as DynamoDB, or fine-grained rights could include read and write access to a specific S3 bucket.
Third, by allowing AWS cloud trail, IAM offers a framework for monitoring and auditing access to specified resources.
Finally, for those of you in large businesses with existing identity solutions, AWS IAM can simply interact with them, so that’s a high-level understanding of what IAM is.
What Is IAM and How Does It Work?
Some groups simply refer to a group of users who have a same interest. Student interns and senior developers are two examples. We want student interns to have permissions that are substantially distinct from those of a senior developer.
Finally, certain jobs serve as a repository for policies. You may create a role with database read and database right rights to a single AWS DynamoDB table, for example. Roles differ slightly in that they are often not attached to specific users and are intended to be assumed by anybody who need them. You may, for example, use roles to provide users from another AWS account access to one of your DynamoDB tables by defining a role with the appropriate permissions and then allowing them the ability to assume or utilise that role.
Finally, some policies are IAM’s bread and butter. These items describe the particular low-level permissions for accessing AWS resources, and they come in two flavours. You can grant or reject permissions to resources using the allow or deny buttons. As an example, here’s a JSON representation of his policy.
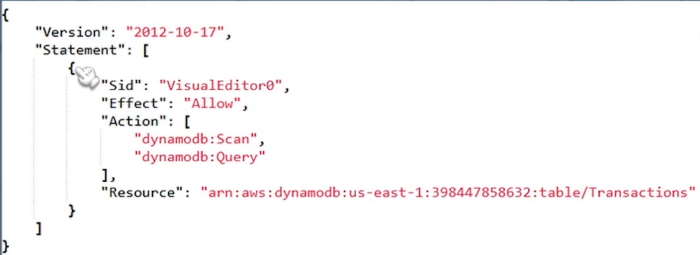
We have a statement ID, which is abbreviated as Sid. It could be anything. We have an effect, which in this case is ‘allow,’ so it may be either ‘allow’ or ‘deny.’ We’ve taken action. These are the precise permissions we’d want to grant. So we have a DynamoDB that needs to be scanned and a DynamoDB that needs to be queried. So, with this policy, just these two permissions are permitted.
There’s also the’resource’ element to consider. In this case, we’re using AWS to provide a certain resource. As a result, this policy or permission only allows users to scan and query this one table. Optionally, you may use a wild card, such as a star, to grant access to all DynamoDB tables to the user who is utilising this policy.
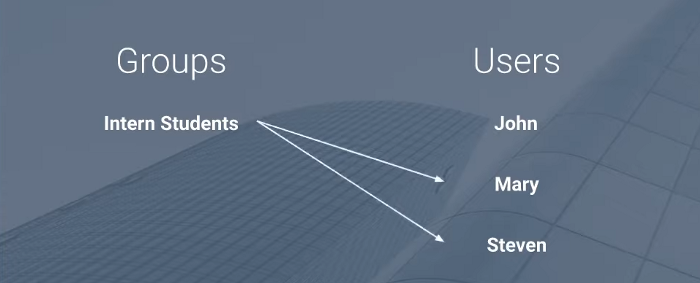
So, in this case, we’re working with a single group, a group of intern students, and we’ve specified three users. John, Mary, and Steven are three friends. Mary and Steven are now student interns, as I said before. I’d want to offer them fewer or more limited rights than the rest of the users. Assume we now have two policies.
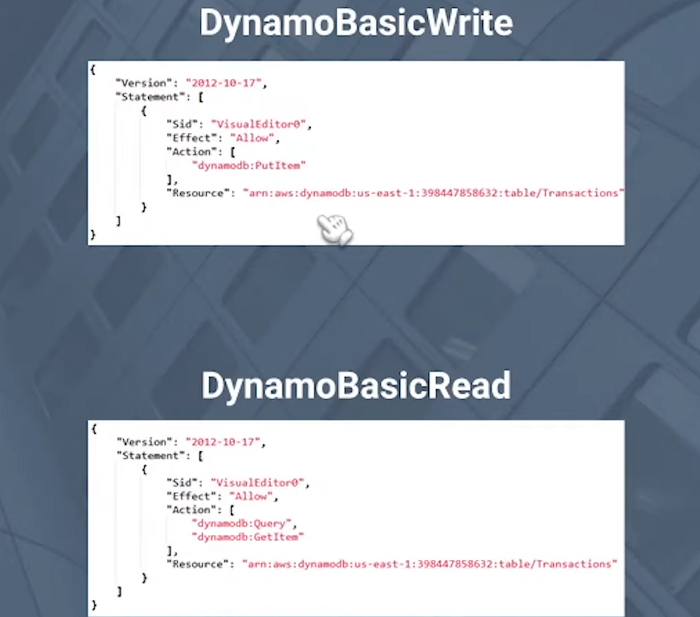
So, we have a DynamoDB basic, which allows us to conduct a put item action on a specified table, correct? Then there’s a DynamoDB basic read, which provides us the query as well as the item permissions on this table. In this case, we’ll link this group to the DynamoDB basic read rights to let Mary and Steven access to the DynamoDB table. And it’s pretty easy to do.
Simply go to the group portion of the AWS interface, add a policy, and choose the policy that contains the rights you require. What about John, who has been left alone? John now wishes to use this table as well. He wants to use the query obtains item API and the put item API.